Table of Content
- 1 Prepare Data for Exploration Module 1 Challenge Answers
- 1.1 Which of the following items are examples of structured data? Select all that apply.
- 1.2 Which of the following items are examples of structured data? Select all that apply.
- 1.3 Fill in the blank: The number of products in a store is an example of _____ data.
- 1.4 Fill in the blank: The number of stars awarded to a product review is an example of _____ data.
- 1.5 Which of the following statements accurately describe first-, second-, and third-party data? Select all that apply.
- 1.6 Which of the following statements accurately describe first-, second-, and third-party data? Select all that apply.
- 1.7 On very short notice, a data analyst is asked to create a report for stakeholders. Because of the challenging time frame, what type of data might yield the best results?
- 1.8 A data analyst at an energy utility wants to study the opinions of all adults in Portugal about green energy. Because It would be impractical to collect data from every single person in the country, the data analyst studies a part of the population that is representative of the whole. What does this scenario describe?
- 1.9 Which of the following items are examples of continuous data? Select all that apply.
- 1.10 What type of data is contained in the following spreadsheet?
- 1.11 Which of the following questions would enable a data professional to collect nominal qualitative data?
- 1.12 A data professional at a social media company records whether users have shared a particular post or not. What data type is being collected in this scenario?
- 2 Prepare Data for Exploration Module 2 Challenge Answers
- 2.1 Legal right to access your data is an element of which aspect of data ethics?
- 2.2 A junior data analyst at a library researches the origin of a dataset to confirm it was created by a reputable source, such as an accredited university. Which aspect of good data are they prioritizing?
- 2.3 A hospital system wants to protect the personally identifiable information of its patients, such as names and medical records. They ask their data team to anonymize the data. What techniques might they use to achieve this goal?
- 2.4 An engineer designs a new application, which receives unclear user ratings. The engineer decides the ambiguous feedback is just a case of users being unfamiliar with the app. What type of bias does this represent?
- 2.5 Which data ethics principle gives an individual the right to know why their data is collected and how it will be used?
- 2.6 A recreation department asks people to respond to a survey about the customer experience in city parks. The survey is only accessible to people who have access to the internet. What type of bias does this scenario describe?
- 2.7 Fill in the blank: The data ethics principle of transaction transparency states that an individual has the right to understand all of the data-processing activities and _____ used on their data.
- 2.8 A government agency allows any business, nonprofit, or citizen to access its databases and reuse or redistribute the data. What type of data is described in this scenario?
- 3 Prepare Data for Exploration Module 3 Challenge Answers
- 3.1 Fill in the blank: Data professionals use data _____ to control their company’s data and make sure data assets are formally managed.
- 3.2 A data analyst at a software company uses metadata to track the source of user bugs in order to troubleshoot the problem. They learn about the device, operating system, and browser on which each bug was encountered. What type of metadata are they using?
- 3.3 Which of the following statements accurately describe primary and foreign keys in a relational database? Select all that apply.
- 3.4 A data analyst runs the following query. What do they want to retrieve from the database?
- 3.5 A junior data professional prepares for an analysis project about a very broad and global topic. However, they will only have access to internal data. What are some potential limitations that they should be aware of? Select all that apply.
- 3.6 A data team at a trade school is sending a text alert to all students who have fewer than 10 credits. What spreadsheet tool will enable them to display only the students who meet that condition?
- 3.7 Which SQL statement will return only elementary school students from the Grade column of the Students database table?
- 3.8 A junior data analyst at a dental care provider uses a tool to explore the data in its patient database. They learn about the data types it contains, the quality of that data, and the table relationships. What does this scenario describe?
- 4 Prepare Data for Exploration Module 4 Challenge Answers
- 4.1 You are the manager of your organization’s monthly purchasing spreadsheet. It has eight sheets, each of which denotes a different department’s purchases. You apply restrictions on the spreadsheet to ensure each department can only access their own sheet. What practice does this scenario describe?
- 4.2 A data analyst collects data from multiple sources for a project involving many other team members. What should the analyst include in each file’s name in order to create a naming convention that allows project files to be located efficiently? Select all that apply.
- 4.3 A data analyst team revisits an old project and wants to understand how the file-naming conventions are structured. Where does the team locate this information?
- 4.4 A grocery store collects inventory data about its produce section. What is an appropriate naming convention for this file?
- 4.5 Fill in the blank: A data team establishes _____ best practices in order to ensure all team members keep project-related files together and organize the correct folders into subfolders.
- 4.6 Fill in the blank: A junior data analyst uses _ to organize files in a way that keeps project-related files together.
- 4.7 A data analyst creates a spreadsheet with five tabs. They want to share only tabs 1-4 with a client because tab 5 contains sensitive information. Which of the following tactics will enable them to keep tab 5 private? Select all that apply.
- 4.8 A data team at a manufacturing company finishes a project about production rates, so they delete the related files. However, they are later tasked with another production project, which the deleted files could have informed. What should the data team have done with the original project files?
- 4.9 Fill in the blank: In an effective ___, subfolders are stored within broader-topic folders in order to help organize files into categories.
Prepare Data for Exploration Module 1 Challenge Answers
Which of the following items are examples of structured data? Select all that apply.
- Audio recording
- Price list
- Data table
- Scanned medical images
or
Which of the following items are examples of structured data? Select all that apply.
- Business notes
- Email message
- Relational database
- Calendar
Fill in the blank: The number of products in a store is an example of _____ data.
- open
- continuous
- nominal
- discrete
or
Fill in the blank: The number of stars awarded to a product review is an example of _____ data.
- nominal
- discrete
- open
- continuous
Which of the following statements accurately describe first-, second-, and third-party data? Select all that apply.
- When using third-party data, it’s important to confirm its accuracy.
- Third-party data is collected by an individual or group using their own resources.
- A key benefit of using first-party data is that the user knows where it came from.
- Second-party data is sold by a trusted partner to another party.
or
Which of the following statements accurately describe first-, second-, and third-party data? Select all that apply.
- Second-party data is often less reliable than third-party data.
- First-party data is collected by an individual or group using their own resources.
- Third-party data comes from outside sources.
- First-, second-, and third-party data should all be checked for accuracy before use.
On very short notice, a data analyst is asked to create a report for stakeholders. Because of the challenging time frame, what type of data might yield the best results?
- Fabricated
- Unclean
- Theoretical
- Historical
A data analyst at an energy utility wants to study the opinions of all adults in Portugal about green energy. Because It would be impractical to collect data from every single person in the country, the data analyst studies a part of the population that is representative of the whole. What does this scenario describe?
- Choosing quantitative data
- Using a population
- Choosing a data type
- Using a sample
Which of the following items are examples of continuous data? Select all that apply.
- Square footage of a house
- Amount of traffic at rush hour
- Number of languages spoken
- Favorite live music venue
What type of data is contained in the following spreadsheet?
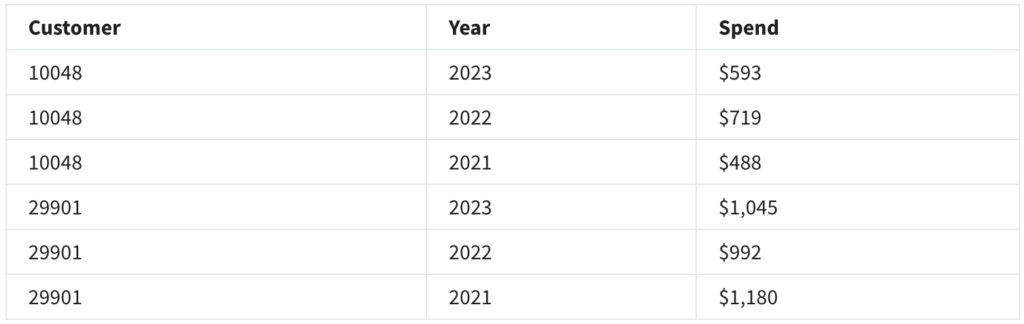
- Unstructured
- Tall
- Long
- Wide
Which of the following questions would enable a data professional to collect nominal qualitative data?
- What is your job title?
- What is your age?
- How many siblings do you have?
- What is your GPA?
- String
- Numerical
- Boolean
- Text
Prepare Data for Exploration Module 2 Challenge Answers
Legal right to access your data is an element of which aspect of data ethics?
- Transparency
- Currency
- Privacy
- Consent
A junior data analyst at a library researches the origin of a dataset to confirm it was created by a reputable source, such as an accredited university. Which aspect of good data are they prioritizing?
- Comprehensive
- Original
- Reliable
- Cited
A hospital system wants to protect the personally identifiable information of its patients, such as names and medical records. They ask their data team to anonymize the data. What techniques might they use to achieve this goal?
- Hashing
- Sorting
- Blanking
- Masking
An engineer designs a new application, which receives unclear user ratings. The engineer decides the ambiguous feedback is just a case of users being unfamiliar with the app. What type of bias does this represent?
- Interpretation
- Observer
- Confirmation
- Sampling
Which data ethics principle gives an individual the right to know why their data is collected and how it will be used?
- Anonymization
- Consent
- Privacy
- Credibility
A recreation department asks people to respond to a survey about the customer experience in city parks. The survey is only accessible to people who have access to the internet. What type of bias does this scenario describe?
- Observer
- Interpretation
- Confirmation
- Sampling
Fill in the blank: The data ethics principle of transaction transparency states that an individual has the right to understand all of the data-processing activities and _____ used on their data.
- standards
- algorithms
- regulations
- data models
A government agency allows any business, nonprofit, or citizen to access its databases and reuse or redistribute the data. What type of data is described in this scenario?
- Allowable
- Closed
- Free
- Open
Prepare Data for Exploration Module 3 Challenge Answers
Fill in the blank: Data professionals use data _____ to control their company’s data and make sure data assets are formally managed.
- aggregation
- strategy
- mapping
- governance
A data analyst at a software company uses metadata to track the source of user bugs in order to troubleshoot the problem. They learn about the device, operating system, and browser on which each bug was encountered. What type of metadata are they using?
- Structural
- Administrative
- General
- Descriptive
Which of the following statements accurately describe primary and foreign keys in a relational database? Select all that apply.
- Primary keys are unique identifiers for each row in a table.
- A foreign key uniquely identifies a record in a relational database table.
- A table can have multiple foreign keys.
- Primary keys cannot contain null or blank values.
A data analyst runs the following query. What do they want to retrieve from the database?
SELECT *
FROM Video_Games
WHERE Creator = ‘Maddox’
- All fields of the video games created by Maddox
- All fields of the video games
- All fields of the video game creators
- All fields of the video games not created by Maddox
A junior data professional prepares for an analysis project about a very broad and global topic. However, they will only have access to internal data. What are some potential limitations that they should be aware of? Select all that apply.
- The data is not owned by the company.
- It will be more difficult to confirm the reliability of the data.
- The data may not fully represent the facts.
- It may be difficult to gather data from multiple departments.
A data team at a trade school is sending a text alert to all students who have fewer than 10 credits. What spreadsheet tool will enable them to display only the students who meet that condition?
- Filter out students who have fewer than 10 credits
- Sort the number of student credits in descending order
- Sort the number of student credits in ascending order
- Filter out students with more than 10 credits
Which SQL statement will return only elementary school students from the Grade column of the Students database table?
- SELECT * FROM Students WHERE Grade = ‘elementary’
- SELECT * WHERE ‘elementary’
- SELECT * FROM Grade = ‘elementary’
- SELECT * FROM Grade WHERE ‘elementary’
A junior data analyst at a dental care provider uses a tool to explore the data in its patient database. They learn about the data types it contains, the quality of that data, and the table relationships. What does this scenario describe?
- Using a metadata repository
- Designing a database
- Performing data analysis
- Combining data from more than one source
Prepare Data for Exploration Module 4 Challenge Answers
You are the manager of your organization’s monthly purchasing spreadsheet. It has eight sheets, each of which denotes a different department’s purchases. You apply restrictions on the spreadsheet to ensure each department can only access their own sheet. What practice does this scenario describe?
- Data preservation
- Data hygiene
- Data security
- Data integrity
A data analyst collects data from multiple sources for a project involving many other team members. What should the analyst include in each file’s name in order to create a naming convention that allows project files to be located efficiently? Select all that apply.
- Collaborator names
- Content description
- Version number
- Creation date
A data analyst team revisits an old project and wants to understand how the file-naming conventions are structured. Where does the team locate this information?
- In SQL
- In folder hierarchies
- In the metadata
- In aggregated data
A grocery store collects inventory data about its produce section. What is an appropriate naming convention for this file?
- Produce_Inventory_2022-09-15_V01
- Inventory_Produce 2022-09-15 V01
- Todays_Produce
- Todays Produce 2022-15-09
- data grouping
- foldering
- data hygiene
- version control
or
- data grouping
- version control
- foldering
- data hygiene
- Hide tab 5, then share the spreadsheet with the client.
- Rename tab 5 to include the word “private,” then share the spreadsheet with the client.
- Make a copy of the spreadsheet, delete tab 5, then share the new file with the client.
- Copy tabs 1-4 into a separate spreadsheet, then share the new file with the client.
- Archive them
- Keep them on their local drive
- Print them out
- Save them on a USB device
Fill in the blank: In an effective ___, subfolders are stored within broader-topic folders in order to help organize files into categories.
- encryption
- file extension
- hierarchy
- permission
